|
The iPhone Wiki is no longer updated. Visit this article on The Apple Wiki for current information. |
Difference between revisions of "T8012"
(Introduced table of T2 devices, checkm8 support) |
m |
||
| (28 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
| − | '''T8012''' is the CPU introduced in the [[J137AP|second-generation iBridge processor]], the processor found on the iMac Pro, and used on all subsequent T2 enabled Mac products. |
+ | '''T8012''', also just known as the '''T2''' is the CPU introduced in the [[J137AP|second-generation iBridge processor]], the processor found on the iMac Pro, and used on all subsequent T2 enabled Mac products. |
== Enabled Mac Products == |
== Enabled Mac Products == |
||
| − | Devices sourced from [https://github.com/libimobiledevice/libirecovery/blob/master/src/libirecovery.c] |
+ | Devices sourced from [https://github.com/libimobiledevice/libirecovery/blob/master/src/libirecovery.c] and [https://dortania.github.io/OpenCore-Post-Install/universal/security/applesecureboot.html] |
{| class="wikitable" |
{| class="wikitable" |
||
| Line 10: | Line 10: | ||
!Board Minor |
!Board Minor |
||
!Description (Product ID) |
!Description (Product ID) |
||
| + | !checkm8/blackbird confirmed |
||
|- |
|- |
||
|iBridge2,1 |
|iBridge2,1 |
||
| + | |J137AP |
||
| − | |j137ap |
||
|0x0A |
|0x0A |
||
|Apple T2 iMacPro1,1 (j137) |
|Apple T2 iMacPro1,1 (j137) |
||
| + | |yes |
||
|- |
|- |
||
|iBridge2,3 |
|iBridge2,3 |
||
| + | |J680AP |
||
| − | |j680ap |
||
|0x0B |
|0x0B |
||
|Apple T2 MacBookPro15,1 (j680) |
|Apple T2 MacBookPro15,1 (j680) |
||
| + | |yes |
||
|- |
|- |
||
|iBridge2,4 |
|iBridge2,4 |
||
| + | |J132AP |
||
| − | |j132ap |
||
|0x0C |
|0x0C |
||
|Apple T2 MacBookPro15,2 (j132) |
|Apple T2 MacBookPro15,2 (j132) |
||
| + | |yes |
||
|- |
|- |
||
|iBridge2,5 |
|iBridge2,5 |
||
| + | |J174AP |
||
| − | |j174ap |
||
|0x0E |
|0x0E |
||
|Apple T2 Macmini8,1 (j174) |
|Apple T2 Macmini8,1 (j174) |
||
| + | |yes |
||
|- |
|- |
||
|iBridge2,6 |
|iBridge2,6 |
||
| + | |J160AP |
||
| − | |j160ap |
||
|0x0F |
|0x0F |
||
|Apple T2 MacPro7,1 (j160) |
|Apple T2 MacPro7,1 (j160) |
||
| + | |yes |
||
|- |
|- |
||
|iBridge2,7 |
|iBridge2,7 |
||
| + | |J780AP |
||
| − | |j780ap |
||
|0x07 |
|0x07 |
||
|Apple T2 MacBookPro15,3 (j780) |
|Apple T2 MacBookPro15,3 (j780) |
||
| + | |yes |
||
|- |
|- |
||
|iBridge2,8 |
|iBridge2,8 |
||
| + | |J140kAP |
||
| − | |j140kap |
||
|0x17 |
|0x17 |
||
|Apple T2 MacBookAir8,1 (j140k) |
|Apple T2 MacBookAir8,1 (j140k) |
||
| + | |yes |
||
|- |
|- |
||
|iBridge2,10 |
|iBridge2,10 |
||
| + | |J213AP |
||
| − | |j213ap |
||
|0x18 |
|0x18 |
||
|Apple T2 MacBookPro15,4 (j213) |
|Apple T2 MacBookPro15,4 (j213) |
||
| + | |yes |
||
| + | |- |
||
| + | |iBridge2,11 |
||
| + | |J230AP |
||
| + | |0x1F |
||
| + | |? |
||
| + | |? |
||
|- |
|- |
||
|iBridge2,12 |
|iBridge2,12 |
||
| + | |J140aAP |
||
| − | |j140aap |
||
|0x37 |
|0x37 |
||
|Apple T2 MacBookAir8,2 (j140a) |
|Apple T2 MacBookAir8,2 (j140a) |
||
| + | |yes |
||
| + | |- |
||
| + | |iBridge2,13 |
||
| + | |J214AP |
||
| + | |0x1E |
||
| + | |? |
||
| + | |? |
||
|- |
|- |
||
|iBridge2,14 |
|iBridge2,14 |
||
| + | |J152fAP |
||
| − | |j152f |
||
|0x3A |
|0x3A |
||
|Apple T2 MacBookPro16,1 (j152f) |
|Apple T2 MacBookPro16,1 (j152f) |
||
| + | |yes |
||
| + | |- |
||
| + | |iBridge2,15 |
||
| + | |J230kAP |
||
| + | |0x3F |
||
| + | |Apple T2 MacBookAir9,1 (j230k) |
||
| + | |yes |
||
| + | |- |
||
| + | |iBridge2,16 |
||
| + | |J214kAP |
||
| + | |0x3E |
||
| + | |Apple T2 MacBookPro16,2 (j214k) |
||
| + | |? |
||
| + | |- |
||
| + | |iBridge2,19 |
||
| + | |J185AP |
||
| + | |0x22 |
||
| + | |Apple T2 iMac20,1 (j185) |
||
| + | |? |
||
| + | |- |
||
| + | |iBridge2,20 |
||
| + | |J185fAP |
||
| + | |0x23 |
||
| + | |Apple T2 iMac20,2 (j185f) |
||
| + | |? |
||
| + | |- |
||
| + | |iBridge2,21 |
||
| + | |J223AP |
||
| + | |0x3B |
||
| + | |Apple T2 MacBookPro16,3 (j223) |
||
| + | |? |
||
| + | |- |
||
| + | |iBridge2,22 |
||
| + | |J215AP |
||
| + | |0x38 |
||
| + | |Apple T2 MacBookPro16,4 (j215) |
||
| + | |? |
||
|} |
|} |
||
| + | |||
| + | ==T2 Recovery USB Device ID== |
||
| + | During the restore process, the T2 presents as a [[Restore Mode]] <code>com.apple.recoveryd</code> service, but uses the USB product ID of <code>0x8086</code> ([https://usb-ids.gowdy.us/read/UD/8086 owned by Intel]) instead of the iPhone's <code>0x1290-0x12AF</code>.[https://github.com/libimobiledevice/usbmuxd/blob/master/udev/39-usbmuxd.rules.in] |
||
==Bootrom Exploits== |
==Bootrom Exploits== |
||
| − | The T8012 uses Bootrom version [[Bootrom_3401.0.0.1.16]] which is vulnerable to [[checkm8]]. A |
+ | The T8012 uses Bootrom version [[Bootrom_3401.0.0.1.16]] which is vulnerable to [[checkm8]]. A fork of [[checkm8]] with support for the t2 exists at [https://github.com/h0m3us3r/ipwndfu h0m3us3r] and a checkra1n with T2 tutorial is at [https://blog.t8012.dev/t2-checkra1n-guide/ t8012 blog]. The adaption of checkm8 was performed by the [[t8012 checkm8]] group by brute forcing the various locations from ROM. The copyright string reads <code>SecureROM for t8012si, Copyright 2007-2016, Apple Inc</code>, for version [[Bootrom_3401.0.0.1.16]]. |
| + | |||
| + | * [https://twitter.com/axi0mX/status/1182915286858522624 axi0mX T2 support tweet] |
||
| + | * [https://twitter.com/qwertyoruiopz/status/1237400943047704576?s=21 quertyoruiop's early checkra1n previews] |
||
| + | |||
| + | Similar to iPhones, iPads, and iPods, iBridge firmware bundles come in IPSW form. Build train codenames are appended with "HWBridge" to distinguish them from normal firmwares, and the disk image files inside have labels that are appended with "UniversalBridgeOS." They can only be restored to if the Mac is in [[DFU mode]]. |
||
| + | |||
| + | === The T2 Secure Enclave Processor (SEP) === |
||
| + | |||
| + | The T2 is based on the A10 silicon design and therefore has a A10 SEP. The A10 SEP is a ARM Cortex-A7 32bit CPU. The T2 Secure Enclave is vulnerable to the same exploit Pangu presented at MOSEC named [[blackbird Exploit|blackbird]]. |
||
| + | |||
| + | The T2 SEP is responsible for acting as a secure store for symmetric secrets (tokens) as well as asymmetric credentials that can be generated and wrapped by the SEP. The SEP plays a key role in disk encryption. |
||
| + | |||
| + | == Entering DFU Mode == |
||
| + | The T2 models can be restored via a Thunderbolt cable using [https://apps.apple.com/us/app/apple-configurator-2/id1037126344?mt=12 Apple Configurator]. |
||
| + | |||
| + | === Desktop Macs === |
||
| + | For example, iMac Pro and Mac mini models from 2018 or later.<ref>https://support.apple.com/en-us/guide/apple-configurator-2/apdebea5be51/mac</ref> |
||
| + | |||
| + | # Completely power off the Mac; disconnect it from external power. |
||
| + | # Attach one end of a Thunderbolt cable to the correct Thunderbolt port on the Mac. |
||
| + | #* iMac Pro: The Thunderbolt port that is located next to the Ethernet port. |
||
| + | #* Mac mini: The Thunderbolt port that is located next to the HDMI port. |
||
| + | # Connect the other end to any Thunderbolt or USB port on the host Mac (the device which will be used for restoring). |
||
| + | # Hold down the power button on the back of the Mac for 3 seconds, while connecting the power cord. |
||
| + | |||
| + | === Portable Macs === |
||
| + | For example, MacBook models from 2018 or later.<ref>https://support.apple.com/en-us/guide/apple-configurator-2/apd0020c3dc2/mac</ref> |
||
| + | |||
| + | # Completely power off the Mac; disconnect it from external power. |
||
| + | # Attach one end of a Thunderbolt cable to the Thunderbolt port that is located on the left side, closest to the front. |
||
| + | # Connect the other end to any Thunderbolt or USB port on the host Mac (the device which will be used for restoring). |
||
| + | # Hold down the power button, right Shift key, and left Control and Option keys, for 3 seconds. |
||
| + | |||
| + | === Identifying the T2 from DFU === |
||
| + | |||
| + | Once a device is in DFU enumerating the USB device yields the BoardID. Using either Linux's <code>lsusb -v</code> or macOS's <code>ioreg -p IOUSB</code> the USB serial attribute will contain the same information as any other Apple A core iBoot device. (http://newosxbook.com/bonus/iBoot.pdf). The ChipID will always be 8012. The value for BDID is the BoardID. Full decoding of the version string can be performed using the code at https://github.com/das-iboot/das-iboot/blob/master/das_iboot/device.py. These values for BDID, CPID, CPRV and ECID are in Hex. |
||
| + | |||
| + | === Identifying the T2 from macOS === |
||
| + | |||
| + | This will provide many of the same values as DFU but in Decimal instead of Hex like above: |
||
| + | |||
| + | <syntaxhighlight lang="bash"> |
||
| + | # ECID in decimal instead of Hex |
||
| + | /usr/libexec/remotectl get-property localbridge UniqueChipID |
||
| + | # Chip ID CPID in decimal (32786 == 0x8012) |
||
| + | /usr/libexec/remotectl get-property localbridge ChipID |
||
| + | # Board Revision CPRV in decimal instead of hex |
||
| + | /usr/libexec/remotectl get-property localbridge BoardRevision |
||
| + | # Board ID (BDID) in decimal instead of hex |
||
| + | /usr/libexec/remotectl get-property localbridge BoardId |
||
| + | # Hardware Model is the name of the Board |
||
| + | /usr/libexec/remotectl get-property localbridge HWModel |
||
| + | # Mac Model String |
||
| + | sysctl -n hw.model |
||
| + | </syntaxhighlight> |
||
| + | |||
| + | == Mac Configuration Utility == |
||
| + | [[Image:MCUIcon.png|thumb|The Mac Configuration Utility icon.]] |
||
| + | |||
| + | In order to restore a firmware to an iBridge device, technicians must use two Apple Internal tools. The first one, '''Apple Service Toolkit (AST)''', is used to initiate a diagnostic session between the host Mac and the Mac in DFU mode. The second tool, which must be installed on the host Mac, is known as the '''Mac Configuration Utility (MCU)'''. It communicates with AST to provide board information and initiate restores and diagnostics over-the-air. MCU supports macOS 10.13.2 or later. |
||
| + | |||
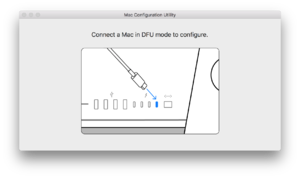
| + | [[Image:MCU.png|thumb|The Mac Configuration Utility startup screen.]] |
||
| + | |||
| + | iBridge devices can still be managed if there is no firmware present by booting a diagnostic image, which is pushed to the device by MCU after a '''Blank Board Serializer''' test is initiated on AST. This test will also assign a serial number to a new board. |
||
| + | |||
| + | During a restore, an Apple logo and progress bar will show on the screen, similar to that of a normal device restore. It is unknown if iBridge firmwares are signed, or if they are verified by the host or by iBridge devices. |
||
| + | == References == |
||
| − | [https://twitter.com/axi0mX/status/1182915286858522624 axi0mX T2 support tweet] |
||
| + | <references /> |
||
| − | {{stub|hardware}} |
||
[[Category:Application Processors]] |
[[Category:Application Processors]] |
||
Latest revision as of 17:41, 17 May 2022
T8012, also just known as the T2 is the CPU introduced in the second-generation iBridge processor, the processor found on the iMac Pro, and used on all subsequent T2 enabled Mac products.
Contents
Enabled Mac Products
Devices sourced from [1] and [2]
| iBridge Product ID | Board ID | Board Minor | Description (Product ID) | checkm8/blackbird confirmed |
|---|---|---|---|---|
| iBridge2,1 | J137AP | 0x0A | Apple T2 iMacPro1,1 (j137) | yes |
| iBridge2,3 | J680AP | 0x0B | Apple T2 MacBookPro15,1 (j680) | yes |
| iBridge2,4 | J132AP | 0x0C | Apple T2 MacBookPro15,2 (j132) | yes |
| iBridge2,5 | J174AP | 0x0E | Apple T2 Macmini8,1 (j174) | yes |
| iBridge2,6 | J160AP | 0x0F | Apple T2 MacPro7,1 (j160) | yes |
| iBridge2,7 | J780AP | 0x07 | Apple T2 MacBookPro15,3 (j780) | yes |
| iBridge2,8 | J140kAP | 0x17 | Apple T2 MacBookAir8,1 (j140k) | yes |
| iBridge2,10 | J213AP | 0x18 | Apple T2 MacBookPro15,4 (j213) | yes |
| iBridge2,11 | J230AP | 0x1F | ? | ? |
| iBridge2,12 | J140aAP | 0x37 | Apple T2 MacBookAir8,2 (j140a) | yes |
| iBridge2,13 | J214AP | 0x1E | ? | ? |
| iBridge2,14 | J152fAP | 0x3A | Apple T2 MacBookPro16,1 (j152f) | yes |
| iBridge2,15 | J230kAP | 0x3F | Apple T2 MacBookAir9,1 (j230k) | yes |
| iBridge2,16 | J214kAP | 0x3E | Apple T2 MacBookPro16,2 (j214k) | ? |
| iBridge2,19 | J185AP | 0x22 | Apple T2 iMac20,1 (j185) | ? |
| iBridge2,20 | J185fAP | 0x23 | Apple T2 iMac20,2 (j185f) | ? |
| iBridge2,21 | J223AP | 0x3B | Apple T2 MacBookPro16,3 (j223) | ? |
| iBridge2,22 | J215AP | 0x38 | Apple T2 MacBookPro16,4 (j215) | ? |
T2 Recovery USB Device ID
During the restore process, the T2 presents as a Restore Mode com.apple.recoveryd service, but uses the USB product ID of 0x8086 (owned by Intel) instead of the iPhone's 0x1290-0x12AF.[3]
Bootrom Exploits
The T8012 uses Bootrom version Bootrom_3401.0.0.1.16 which is vulnerable to checkm8. A fork of checkm8 with support for the t2 exists at h0m3us3r and a checkra1n with T2 tutorial is at t8012 blog. The adaption of checkm8 was performed by the t8012 checkm8 group by brute forcing the various locations from ROM. The copyright string reads SecureROM for t8012si, Copyright 2007-2016, Apple Inc, for version Bootrom_3401.0.0.1.16.
Similar to iPhones, iPads, and iPods, iBridge firmware bundles come in IPSW form. Build train codenames are appended with "HWBridge" to distinguish them from normal firmwares, and the disk image files inside have labels that are appended with "UniversalBridgeOS." They can only be restored to if the Mac is in DFU mode.
The T2 Secure Enclave Processor (SEP)
The T2 is based on the A10 silicon design and therefore has a A10 SEP. The A10 SEP is a ARM Cortex-A7 32bit CPU. The T2 Secure Enclave is vulnerable to the same exploit Pangu presented at MOSEC named blackbird.
The T2 SEP is responsible for acting as a secure store for symmetric secrets (tokens) as well as asymmetric credentials that can be generated and wrapped by the SEP. The SEP plays a key role in disk encryption.
Entering DFU Mode
The T2 models can be restored via a Thunderbolt cable using Apple Configurator.
Desktop Macs
For example, iMac Pro and Mac mini models from 2018 or later.[1]
- Completely power off the Mac; disconnect it from external power.
- Attach one end of a Thunderbolt cable to the correct Thunderbolt port on the Mac.
- iMac Pro: The Thunderbolt port that is located next to the Ethernet port.
- Mac mini: The Thunderbolt port that is located next to the HDMI port.
- Connect the other end to any Thunderbolt or USB port on the host Mac (the device which will be used for restoring).
- Hold down the power button on the back of the Mac for 3 seconds, while connecting the power cord.
Portable Macs
For example, MacBook models from 2018 or later.[2]
- Completely power off the Mac; disconnect it from external power.
- Attach one end of a Thunderbolt cable to the Thunderbolt port that is located on the left side, closest to the front.
- Connect the other end to any Thunderbolt or USB port on the host Mac (the device which will be used for restoring).
- Hold down the power button, right Shift key, and left Control and Option keys, for 3 seconds.
Identifying the T2 from DFU
Once a device is in DFU enumerating the USB device yields the BoardID. Using either Linux's lsusb -v or macOS's ioreg -p IOUSB the USB serial attribute will contain the same information as any other Apple A core iBoot device. (http://newosxbook.com/bonus/iBoot.pdf). The ChipID will always be 8012. The value for BDID is the BoardID. Full decoding of the version string can be performed using the code at https://github.com/das-iboot/das-iboot/blob/master/das_iboot/device.py. These values for BDID, CPID, CPRV and ECID are in Hex.
Identifying the T2 from macOS
This will provide many of the same values as DFU but in Decimal instead of Hex like above:
# ECID in decimal instead of Hex
/usr/libexec/remotectl get-property localbridge UniqueChipID
# Chip ID CPID in decimal (32786 == 0x8012)
/usr/libexec/remotectl get-property localbridge ChipID
# Board Revision CPRV in decimal instead of hex
/usr/libexec/remotectl get-property localbridge BoardRevision
# Board ID (BDID) in decimal instead of hex
/usr/libexec/remotectl get-property localbridge BoardId
# Hardware Model is the name of the Board
/usr/libexec/remotectl get-property localbridge HWModel
# Mac Model String
sysctl -n hw.model
Mac Configuration Utility
In order to restore a firmware to an iBridge device, technicians must use two Apple Internal tools. The first one, Apple Service Toolkit (AST), is used to initiate a diagnostic session between the host Mac and the Mac in DFU mode. The second tool, which must be installed on the host Mac, is known as the Mac Configuration Utility (MCU). It communicates with AST to provide board information and initiate restores and diagnostics over-the-air. MCU supports macOS 10.13.2 or later.
iBridge devices can still be managed if there is no firmware present by booting a diagnostic image, which is pushed to the device by MCU after a Blank Board Serializer test is initiated on AST. This test will also assign a serial number to a new board.
During a restore, an Apple logo and progress bar will show on the screen, similar to that of a normal device restore. It is unknown if iBridge firmwares are signed, or if they are verified by the host or by iBridge devices.